You’ve Got Spam!
Posted on: March 16, 2008
The following is a paper I wrote on spam for an assignment. Please take a look.
A 2004 report from the firm Message Labs estimated that spam accounted for 80 percent of international email traffic, 10 percent higher than 2000 (Task Force On Spam, 2005). While there is no fixed definition, nor agreed-upon date of the birth of spam, it is agreed widely (as will be demonstrated) that spam is a serious problem causing heavy financial loss and decreased productivity (Boone-Lutz, 2007). Spam intrudes privacy of individual users and companies allowing for potential theft of information considered private under various Bills and Acts in different countries. While work is being done at all levels to combat the problem of spam, it is not sufficient. As spam continues to increase in its proliferation and damage, these efforts need to be stepped up equally. Jamie De Guerre, in an interview with Internetnews.com stated that “attackers are [growing] increasingly advanced and the current security model can’t keep up.” (Scannell, 2006). In this paper I will attempt to define spam and discuss its origin. I will then move on to its categorization, followed by both technological measures and government initiatives to fight spam. I will then discuss if these measures are sufficient and if not, what further needs to be done.
There is no fixed definition of the word spam. Some limit spam to any unsolicited commercial or bulk emails, while others adapt a broader definition, including any sort of unwanted messages (Acharya, 2004) whether they are email, cell phone messages or even hoardings. In essence, spam tries to sell an individual a product or service which the individual may or may not want and may even object to due to its explicit nature. Mails are sent out in bulk with no targeted audience, rendering identity and context irrelevant. Emails may also be classified as spam if the recipient has not granted permission for them to be sent (Tanzila, 2006).
There is no fixed, agreed-upon originating date of spam: some say it dates as far back as the internet itself, while others say it started during the era of the MUDs (Multi User Dungeon) community (Tanzila, 2006).
So where does spam come from? Tanzila notes that spammers access user information from a number of sources in various ways. The most common is email addresses listed on websites, newsgroups, online directories, discussion boards and chat rooms. Other methods include a technique called harvesting, whereby robots “gather e-mail addresses from the web, spotting them by looking for the ‘@’ sign.” Also, mailing lists such as the Yahoo! mailing list receive high amounts of spam. Tanzila reiterates Bradley’s findings, saying that spammers may be able to target as many as twenty thousand people from just twenty mailing lists. When an individual tries to unsubscribe from such mailing lists, it lets the spammers know that the email address is active, and thus becomes a target of even more spam (Tanzila, 2006).
Among various methods of sending spam, a common one relies on the end users’ lack of knowledge of open internet ports. An open port allows spammers to access a computer connected to the internet and send spam through these relays (Tanzila, 2006).
Another common approach is a dictionary method whereby spammers guess different email addresses by “altering names through obvious patterns” to come up with email addresses that may or may not exist (Tanzila, 2006).
There are various types of spam that exist, evolving over time alongside the methods and technologies which are employed to counter it. Nigerian bank schemes are usually emails from someone claiming to be part of a government or a bank who is willing to give away large sums of money to be transferred to the recipient’s bank account. Various other versions exist, such as some claiming to be dying of a terminal illness who would like to “donate” their savings. If the recipient falls prey, they give away their own bank account details unaware of the consequences. Other variations include phishing schemes which claim that there is a problem with the recipient’s bank account asking to confirm credentials. (Tanzila, 2006).
Another breed of spam is credit cards for people with a bad credit line. These schemes usually ask for high upfront processing fees, and as Rimmer notes, one may “end up with nothing or a card that can only be used to purchase items from a single catalogue.” (Tanzila, 2006).
Other categories of spam emails include pornography and health related products, many of which sell drugs such as Viagra at lower rates than the market, however, many a times, these are just shams targeted at unsuspecting victims (Tanzila, 2006).
With spam increasing at a rapid pace, evolving over time, there is no doubt that it has significant impacts from the end-user to multinational corporations. One of the basic problems at the most fundamental levels is that spam “makes the internet less friendly and email less useful.” (Boone-Lutz, 2007). Pop up advertisements and flashing banners have always been a nuisance as it retracts from the overall experience of the online world. However, with spam, torment has reached users’ inboxes, and coupled with the problem of sorting through junk email, sixty percent of users now use email less due to spam, while many others avoid giving out their email addresses to acquaintances or online. This has undermined the internet, bringing it to the verge of imploding with great threat particularly to the institution of email (Boone-Lutz, 2007).
Boone-Lutz also demonstrates the economic cost of spam: he relates spam to “negative externalities,” something which has negative spill-over effects to third-party individuals, usually in monetary and man-power terms. Boone-Lutz informs us that businesses incurred costs between $10 billion and $87 billion in the United States to combat spam and the estimated figure for 2007 was as high as $113 billion (Boone-Lutz, 2007).
Costs are also incurred in terms of time. Recipients of spam cannot avoid it from arriving in their inbox (despite prevention methods, both technological and legal) and spend time “accessing, reviewing and discarding” it (Boone-Lutz, 2007). This leads to even more monetary costs in terms of larger storage space, filtering software, and higher connectivity charges (due to extra time spent on the internet) (Boone-Lutz, 2007).
However, these costs are also sustained beyond the user end. ISP’s too incur heavy costs due to upgrades, additional staff, developing or buying licences to filtering technologies. The additional cost is inevitably passed down to consumers who may decide to change services due to higher prices and/or spam solutions failing altogether. This leads to reduced productivity and loss of labour hours since no filtering technology is perfect. Problems known as under- or over-blocking (where spam is either blocked insufficiently, or is blocked alongside important email) leads to manual checks other than time and money already spent on technologies. Time is also spent in upgrading the equipment as mentioned above, ensuring its smooth functioning, developing solutions in-house and dealing with customers (Boone-Lutz, 2007).
Boone-Lutz also documents spam as a conduit for criminal activities. Essentially, these are fraud or false messages intended to trick the recipient. He states that a Federal Trade Commission study showed that “60% of spam messages contained some form of falsehood,” the most common being the Nigerian Bank scam (Boone-Lutz, 2007). Furthermore, spam is used to collect information of individuals for identity theft purposes. When victims purchase items offered in spam messages, they give away sensitive information such as bank details allowing identity hi-jacking (Boone-Lutz, 2007).
With all of this in mind, coupled with statistics which expose the grave situation, it is no surprise that everyone from end-users, to corporations to governments are playing their part in combating spam, trying to crack down on the issue. Eighme asserts that any technological defense against spam is never 100% effective and thus individuals and firms need to combine various services and softwares for best results. Eighme sorts spam-filtering techniques into four categories, namely heuristic analysis, Bayesian filtering, signature matching, and traffic-pattern analysis (Eighme, 2006).
Heuristic analysis uses “rules” which evaluate emails to grade them as either spam or not spam. Eighme gives an example of a “spam friendly” state where an email originating from a country which is known to send spam violates the “place-of-origin” rule. The frequency of “$” signs used, number of links such as “click here,” capital letters in the subject line, all are part of heuristic analysis. Based on the above conditions, the system grades the email, and if the points exceed the limit point set by the company, the email is marked as spam (Eighme, 2006).
Eighme then moves on to talk about Bayesian filtering. This system too works on the scoring system similar to heuristic analysis. The filter uses a company’s collected sample 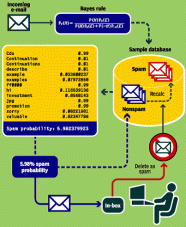 of spam emails to legitimate emails. The words in the legitimate emails are scored based on the frequency of appearance in the sample list. Words that normally appear in spam receive a higher score than words which appear in legitimate email. The mails are then filtered out depending on the borderline score set by the company (Eighme, 2006).
of spam emails to legitimate emails. The words in the legitimate emails are scored based on the frequency of appearance in the sample list. Words that normally appear in spam receive a higher score than words which appear in legitimate email. The mails are then filtered out depending on the borderline score set by the company (Eighme, 2006).
Signature matching uses email accounts that solely collect spam and are monitored by a software or service. The messages received have unique “fingerprints” or markers that identify the email. These markers are collected and stored and markers from incoming mail are compared to this database: if they match, the mail is flagged as spam (Eighme, 2006).
Traffic-pattern analysis is slightly more complicated, targeting the behaviour of spam. Eighme states that, depending on the volume of emails sent out, a message may be classified as spam. Also, emails that are sent out to many invalid addresses and re-route to hide the spammer’s identity also raise flags (Eighme, 2006).
Home users usually have spam-filtering software at their disposal, and according to Eighme, these software filter 90% of all spam, mistaking legit email as spam only 4% of the time. These softwares use the heuristic analysis and Bayesian filtering approach to counter spam. Eighme notes that spammers constantly change their tactics to undermine these softwares so updates are necessary which may be available with subscriptions. Desktop softwares allow users a great deal of flexibility in terms of countering and controlling spam and reducing mistakes made by setting domains and email addresses in a “whitelist” which never get blocked. They also allow users to decide what action to take with spam: delete, quarantine or deliver (Eighme, 2006).
Larger organizations may use what Eighme calls “gateway software” which allow companies to stop spam at the point where it tries to enter into the company network through the internet. This saves a company significant time, labour and hence, money since universal policies can be set and applied to all email addresses of the company as opposed to individually setting each email. These are effective also because they guard the network from malicious attacks by spammers at the entry point. These are usually more effective since they use more advanced technologies like signature matching, and filter 95% of spam, with an incorrect mark at 1 in 10,000 emails (Eighme, 2006).
Another very interesting technology is Vipul’s Razor. Unlike softwares and corporate services, this technology relies on the “wisdom of crowds,” where a community of  individual from all over the globe participate in combating spam. According to Jamie De Guerre, the community consists of trusted users whose “collaborative human intelligence identifies a message as spam, and an automated technology verifies and prevents its proliferation.” (De Guerre, 2007). De Guerre demonstrates that a user base (which was once 10,000 and has increased to 180 million spanning 163 countries) votes on messages that may be considered spam, with users rising on the trust level for every spam message they flag. Essentially, gaining trust is hard, but losing it is easy, so users are deterred from marking them incorrectly. Based on the confidence level of a spam message, the fingerprints are stored in a database which is constantly updated, allowing for a very accurate spam-filtering solution (De Guerre, 2007).
individual from all over the globe participate in combating spam. According to Jamie De Guerre, the community consists of trusted users whose “collaborative human intelligence identifies a message as spam, and an automated technology verifies and prevents its proliferation.” (De Guerre, 2007). De Guerre demonstrates that a user base (which was once 10,000 and has increased to 180 million spanning 163 countries) votes on messages that may be considered spam, with users rising on the trust level for every spam message they flag. Essentially, gaining trust is hard, but losing it is easy, so users are deterred from marking them incorrectly. Based on the confidence level of a spam message, the fingerprints are stored in a database which is constantly updated, allowing for a very accurate spam-filtering solution (De Guerre, 2007).
The technological methods to control spam can only be so effective. In order to control spam at the grassroots level, at the originating point, governments and international agencies have started taking action.
In the United States, The Controlling the Assault of Non-Solicited Porn and Marketing Act (CAN-SPAM) took effect in January 2004 which requires messages to be labelled appropriately with an opt-out option as well as the sender’s physical postal address. It also requires that subject lines and headers not be misleading with fines and jail time for those who fall in contravention. Although this approach still allows for unsolicited, commercial email to be sent, it restricts its ability to cause damage (Acharya, 2004).
Although, Canada does not yet have a legislature in effect to control spam, Acharya informs us that most spam in Canada is not illegal, however, fraudulent emails may be targeted under Canada’s Criminal Code. A bill proposed in the Parliament, also referred to as the Spam Control Act, instituted a no-spam list, with an opt-out option. The spam filter would follow a heuristics approach to be adopted by the members, with punishment including fines and imprisonment. Although this act has yet to be enacted, an amendment to the Criminal Code allowed for the inclusion of “sending unsolicited, commercial electronic email” and the trade of email addresses without permission from those whose email addresses are being sold (Acharya, 2004).
What is important to note here is that the amendment recognized the need for international cooperation (Acharya, 2004). This is no surprise since the internet is virtually without borders, with a lot of spam originating from foreign countries. Boone-Lutz informs us that the recognition of the issue that local policies and measures to combat spam are insufficient, “has led to a variety of developments, including summits, mutual assistance agreements and technical recommendations.” (Boone-Lutz, 2007).
For example, the Organisation for Economic Co-operation and Development (OECD) initiated its Spam Task Force in order to “coordinate international policy responses…and to facilitate cross border law enforcement” amongst its member states (Boone-Lutz, 2007). It released a toolkit which would allow for understanding of the problem of spam and coming to a shared solution. Other initiatives as such have included the Asia-Pacific Economic Cooperation (APEC)’s Lima Declaration, and the United Nation’s International Telecommunications Union’s Plan of Action (Boone-Lutz, 2007).
Other countries have come to bilateral agreements such as the Korea-Australia Memorandum of Understanding. While these summits and bilateral understandings are a step further in combating the problem of fraud and spam, they are not sufficient. Multilateral agreements have therefore been the next step in setting an international standard. One such agreement is the London Action Plan “which called for ‘the creation of an international working group on spam enforcement’” and included 19 agencies that would tackle the problem of spam. This led to investigations in over 300 spam-related cases across the members of the agreement and China’s adopting the Action Plan (Boone-Lutz, 2007).
While other multilateral agreements such as the CAPTEF Declaration and Seoul-Melbourne Agreements exist, Boone-Lutz informs us that “the current patchwork of agreement lacks the force and effectiveness of a true treaty.” Spam has yet not decreased in its proliferation, despite the summits, bilateral and multilateral agreements that have taken place. Spam has compromised 76 percent of all emails worldwide according to a United Nations report. A SophosLabs’ security report stated that Canada fell from being 5th to being 17th in terms of spam messages received (Stop Spam Here, 2007). Other reports say that spam has actually decreased (Swartz, 2006). There is also disparity between figures estimating losses incurred due to spam. All this demonstrates that there is a further need to come to a universal solution to combating the issue with stricter laws and uniform policies. The problem can no longer sit on the sidelines of any state’s agenda. A report from the Task Force on Spam in Canada suggests stricter punishment and enforcement to reduce spamming activities. At the same time it recognizes the need for public education. It mentions that a report published by the National Cyber Security Alliance showed that “80 percent of American users had spyware or adware on their computer”, while 89 percent of those were not aware (Task Force on Spam, 2005). Coupling all of these possible solutions will inevitably lead to the figures going down and sustaining them at very low levels.
Image courtesies of Spam Filter Express and Cloudmark.
7 Responses to "You’ve Got Spam!"
Nice writing style. Looking forward to reading more from you.
Chris Moran
[…] post by Design, Photograph, Communicate Share and Enjoy: These icons link to social bookmarking sites where readers can share and […]
[…] This cup of tea was served by: Design, Photograph, Communicate […]
Hi
Nice Article ,Can I get the references you used for your work.
Thanx
AP
March 16, 2008 at 8:00 am
Excellent Blog. I’ve been reading along and just wanted to say hi. I will be reading more of your posts in the future.
– Jason.